In my previous post "ITIL, ISO 20000, ISO 27001 what else is there?" I have mentioned 36 different frameworks connected to IT Service Management that can be used in everyday working.
Interestingly none of them explicitly mentions security using cloud services. Not even ITIL , ISO 20000:2011 or ISO 27001:2005. ISO 27001:2013, expected to come out at the end of this year, will try to bring change to this, it will separate two domains and create a new one on Provider Relations to cover cloud area. The framework is called COSO’s Enterprise Risk Management – Integrated Framework. COSO stands for Committee of Sponsoring Organizations of the Treadway Commission and it is American private sector joined initiative dedicated to development of comprehensive frameworks and guidance on enterprise risk management, internal control, and fraud deterrence designed to improve organizational performance and governance and to reduce the extent of fraud in organizations.What is this framework about? The framework put forth in COSO’s Enterprise Risk Management – Integrated Framework has established a common language and foundation that can be used to construct an effective cloud governance program tailored specifically for a given cloud solution.
In the picture below, the framework is represented as a pathway in which each ERM component (starting with internal environment) is applied in order to understand the specific advantages and disadvantages that a given solution candidate would bring to the organization. When the process is completed for each cloud solution candidate, the ideal cloud solution will emerge along with its related requisites for establishing cloud governance. In cases where a cloud solution has already been implemented, the COSO ERM framework can be used to establish, refine, or perform a quality assurance check of the cloud governance program by ensuring that all major aspects of the program (e.g., objectives, risk assessment, and risk response) have been addressed with respect to management’s requirements.
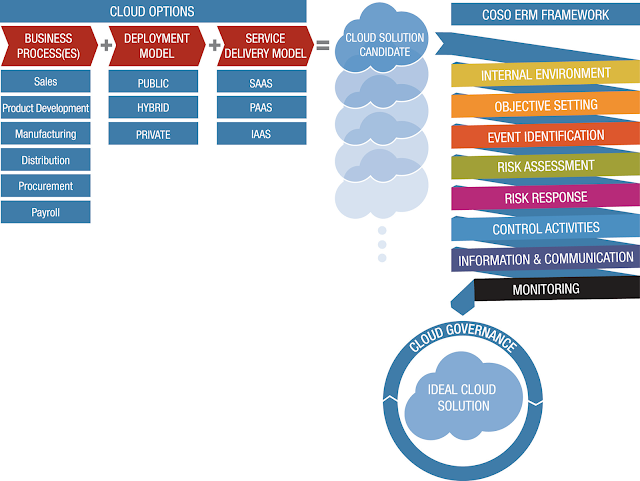 |
| COSO ERM Framework to Cloud Computing Options |
The ERM framework components:
- Internal Environment – The internal environment component serves as the foundation for and defines the organization’s risk appetite in terms of how risks and controls are viewed. For instance, if management has a policy of not outsourcing any of its operations (i.e., there is a culture of risk avoidance), this policy will limit the viable options for cloud deployment and service delivery models so that private cloud solutions might be the only acceptable alternative.
- Objective Setting – Management needs to evaluate how cloud computing aligns with the organization’s objectives. Depending on the circumstances, cloud computing might present an opportunity for the organization to enhance its ability to achieve existing objectives, or it might present an opportunity to gain a competitive advantage, which would require new objectives to be defined.
- Event Identification – Management is responsible for identifying the events (either opportunities or risks) that can affect the achievement of objectives. The complexity of event identification and risk assessment processes increases when an organization engages cloud service providers.
- Risk Assessment – Management should evaluate the risk events associated with its cloud strategy to determine the potential impact of the risks associated with each cloud computing option. Ideally, risk assessments should be completed before an organization moves to a cloud solution.
- Risk Response – Once risks have been identified and assessed in the context of organizational objectives relative to cloud computing, management needs to determine its risk response. There are four types of risk responses: avoidance, reduction, sharing and acceptance.
- Control Activities – The traditional types of controls –preventive, detective, manual, automated, and entity-level – apply to cloud computing as well. The difference introduced by cloud computing is that some control responsibilities might remain with the organization while certain control responsibilities will be transferred to the CSP. If the quality of an organization’s existing control activities is moderate or poor, going to a cloud solution could exacerbate internal control weaknesses. For example, if an organization with poor password controls or data security practices migrates its computing environment to a public or hybrid cloud solution, the possibility of an external security breach is likely to increase significantly due to the fact that access to the organization’s technology base is now through the public Internet.
- Information and Communication – To effectively operate its business and manage the related risks, management relies on timely and accurate information and communications from various sources regarding external and internal events. With cloud computing, information received from a CSP might not be as timely or of the same quality as information from an internal IT function. As a result, fulfilling management’s information and communications requirements might require additional or different information processes and sources.
- Monitoring – “Risk responses that were once effective may become irrelevant; control activities may become less effective, or no longer be performed; or entity objectives may change.” That statement from 2004 in the COSO’s Enterprise Risk Management – Integrated Framework remains applicable in the age of cloud computing. Management must continue to monitor the effectiveness of its ERM program to verify that the program adequately addresses the relevant risks and facilitates achieving the organization’s objectives.
What are some of the risks applicable to the cloud environment?
- Disruptive force - Facilitating innovation (with increased speed) and the cost-savings aspects of cloud computing can themselves be viewed as risk events for some organizations
- Residing in the same risk ecosystem as the CSP and other tenants of the cloud
- Lack of transparency
- Reliability and performance issues
- Vendor lock-in and lack of application portability or interoperability
- Security and compliance concerns
- High-value cyber-attack targets
- Risk of data leakage
- IT organizational changes
- Cloud service provider viability
Before proceeding to the cloud environment be able to give answers to the following question connected to the data and the cloud provider
- Which services and related data can be moved safely into the cloud, and when?
- How will sensitive data be protected in storage, in transit, and in use?
- How can access to cloud-based data and services through new hard-to-control devices such as smartphones and iPads be managed in line with security requirements?
- What security levers built into cloud architecture components can be pulled to mitigate new risks?
- How can companies be sure that cloud service providers are compliant with their security requirements?
- Are industry-recognized security standards applicable?
- Will the incremental cost of cloud security potentially offset the commercial benefits?
If you want to read more about the COSO’s Enterprise Risk Management you can download the following paper: COSO ERM Framework






Data security standards are likely to be higher in your provider’s environment than in your business, especially if the cloud provider is accredited with ISO and other key industry standards.Your cloud provider is likely to be better resourced physically and financially, to cope with data security threats to its infrastructure than you.
ReplyDeleteonline data room providers
https://www.ryanic.com/2018/11/high-availability-and-load-balanced.html?showComment=1568282364613#c3412962161778476926
ReplyDeleteWhen a blind man bears the standard pity those who follow…. Where ignorance is bliss ‘tis folly to be wise…. Links Locksmith Services has a website https://www.linkslocksmith.com
ReplyDeleteThe calling of data innovation centers around PC forms. Appropriate preparing shows understudies how to deal with every one of the parts of data related to innovation.information technology
ReplyDeleteI would also motivate just about every person to save this web page for any favorite assistance to assist posted the appearance. Security Assessments
ReplyDeleteAlways so interesting to visit your site.What a great info, thank you for sharing. this will help me so much in my learning Troll
ReplyDeletei never know the use of adobe shadow until i saw this post. thank you for this! this is very helpful. eidas signature
ReplyDeleteMr. Dinnerman has employed many security officials in Los Angeles and is continually endeavoring to make our locale a more secure spot to live and work.Security Concierge Mississauga
ReplyDeleteThank you for making my own students have access to your site post. Your kindness is greatly appreciated. I’ve some ongoing assignments and I wanted them to assist me with it. The only way they were able to achieve that was carry out some homework on the internet so as to help make my work faster. They came across your site as well as content on it, particularly this blog post, really helped them to get good conclusions on those things we needed to perform. Of course, I will continue to really visit the site for brand new updates on this top and other issues of curiosity. Cloud Servers
ReplyDeleteTook me time to read all the comments, but I really enjoyed the article. It proved to be Very helpful to me and I am sure to all the commenters here! It’s always nice when you can not only be informed, but also entertained! فناوری اطلاعات
ReplyDeleteI really loved reading your blog. It was very well authored and easy to understand. Unlike other blogs I have read which are really not that good.Thanks alot! https://avincenna.com/fresh-alternatives-inside-residence-basic-safety/
ReplyDeleteAmong the mediator benefits that could add expenses to internet business exchanges are promoting, secure online installment, and conveyance. The overall simplicity of turning into an online business shipper and setting up stores brings about such countless contributions that purchasers can undoubtedly be overpowered. Alfresco Training
ReplyDeleteHey, I am so thrilled I found your blog, I am here now and could just like to say thank for a tremendous post and all round interesting website. Please do keep up the great work. I cannot be without visiting your blog again and again. empresa de vigilancia y seguridad
ReplyDeleteYes i am totally agreed with this article and i just want say that this article is very nice and very informative article.I will make sure to be reading your blog more. You made a good point but I can't help but wonder, what about the other side? !!!!!!Thanks wifi cameras
ReplyDeletesdfgfdfg
ReplyDeleteHowever from the definitions over, that is obviously not the situation.Access Control System
ReplyDeleteOn that website page, you'll see your description, why not read through this. https://onohosting.com/
ReplyDeleteCloud hosting is the trendy expression of the town. The purpose for this is its simplicity of scale, adaptability, and superior. There are numerous advantages offered by cloud workers when contrasted with conventional hosting. https://onohosting.com/
ReplyDeleteI can’t imagine focusing long enough to research; much less write this kind of article. You’ve outdone yourself with this material. This is great content. https://hostinglelo.in/
ReplyDeleteA good web host is the secret to the success of your online business. Whether you have a personal website or a corporate/business site, the services and applications offered by your hosting account is the power house of your site. Before you host your site you should read this article. It will help you with tips on how to choose your host. https://onohosting.com/
ReplyDeleteIn the world of www, there are countless blogs. But believe me, this blog has all the perfection that makes it unique in all. I will be back again and again. https://onohosting.com/
ReplyDeleteReselling is basically a process which involves using the resources of parent web hosting companies and selling it as one of their own. Most of the hosting companies today have reseller web hosting packages that you can buy. There are a number of benefits you can get by hosting your website with a reseller. https://hostinglelo.in/
ReplyDeleteGone are the large upfront costs with various consultancy fees and maintenance costs associated with adapting a new application company-wide. free restream review
ReplyDeleteThis is such a great resource that you are providing and you give it away for free. I love seeing blog that understand the value. Im glad to have found this post as its such an interesting one! I am always on the lookout for quality posts and articles so i suppose im lucky to have found this! I hope you will be adding more in the future... Serious Security CCTV Sydney
ReplyDeleteNo Deposit Casinos 2020 (Review 2021) - DrmCD
ReplyDeleteHere you will find the top 10 세종특별자치 출장샵 No 서산 출장샵 Deposit Casinos 2021. 창원 출장안마 Top 충주 출장샵 Free Spins. 1. Vegas Crest Casino. 2. SlotWolf 의정부 출장마사지 Casino. 5. Royal Ace Casino.
Cool
ReplyDelete